When you research cybersecurity, a lot of writers use the terms malware and virus interchangeably. It can be really confusing to then determine what programs or protections you need in place to protect yourself and your business. So, we’re here to clear it up once and for all.
What is malware, and is it the same as a virus?
Malware is a portmanteau of “malicious software”. It means any code that was written with malicious intent. One type of malware is a virus, so named because once it infiltrates a computer, it reproduces & spreads like a biological virus. There are many types of viruses & all are considered malware.
While viruses are one type of malware, there are many more that are just as insidious and potentially damaging to small businesses. Not to mention the common viruses that people encounter online. Read on to learn more!
Common Types of Malware
All Viruses Are Malware, But Not All Malware Are Viruses
As we mentioned in the beginning of this post, malware is a broad term that is designed to disrupt, damage, or gain unauthorized access to a computer system. While viruses are a very prevalent type of malware, there are others that you should know how to recognize.
Falling prey to any one of these types of malware could result in data loss, financial loss, reputational loss, and even business closure. It’s crucial that you and your staff become familiar with the ways these malware work and know what red flags to look out for!
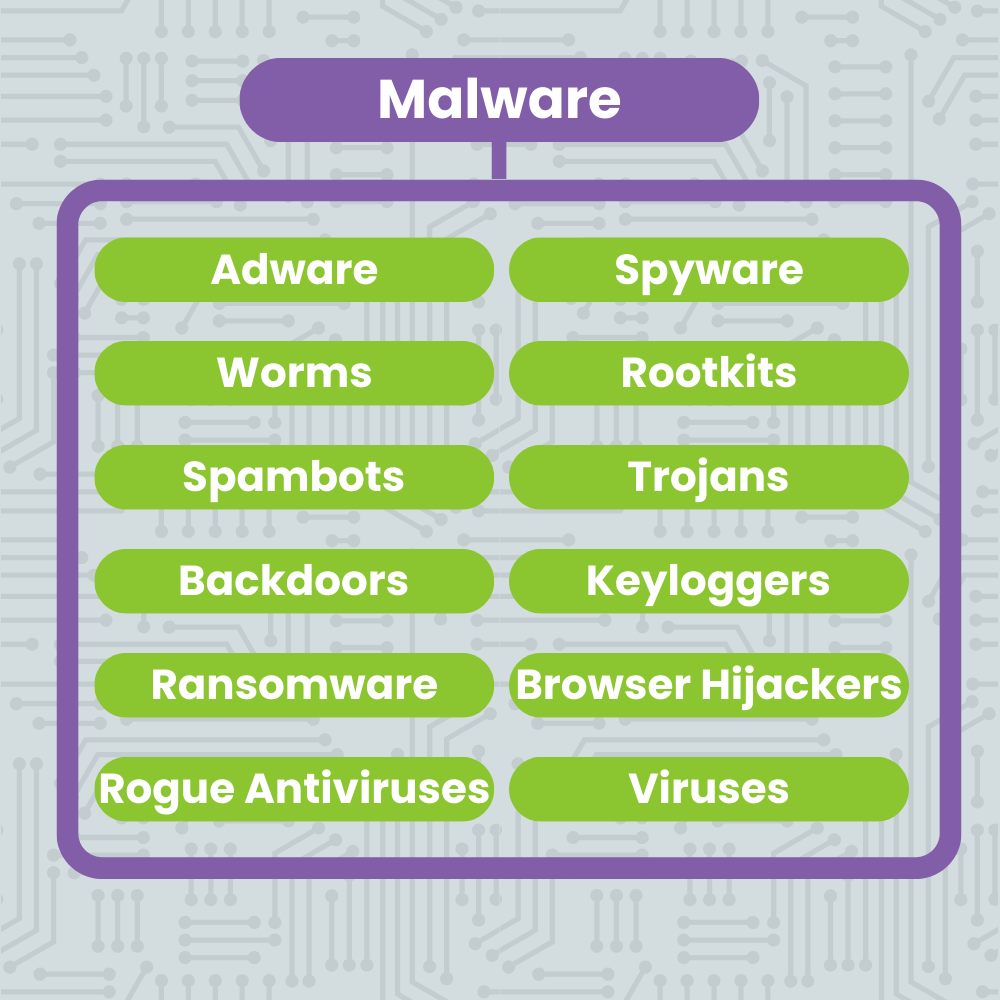
Adware
This type of malware occurs in the form of persistent and pervasive pop-ups. Often, they’ll appear as you’re going about normal internet browsing, and block the things you’re trying to click on.
It’s very important that you avoid clicking on these ads. If you’re lucky they’ll just slow down your computer. If you’re not, accidentally clicking one of these pop-ups could download spyware. Utilizing an adblocker can help to avoid this pitfall.
Spyware
Spyware is a type of malware that monitors the activity of the computer it’s installed on. It is typically used to gather personal data, financial data, or usernames and passwords. This information is then used in other crimes.
Worms
These are similar to computer viruses in that once they infect a computer, they replicate and spread. However, there’s one important difference: they lack a trigger. So, the spreading process begins instantaneously. Admittedly, these have fallen out of vogue a bit, but it’s not outside of the realm of possibility that you’ll encounter.
Rootkits
Rootkits are a type of malware that allow cybercriminals to access your computer remotely without you being made aware of it. Once it’s installed, it can even download other files or change your basic system configuration – which makes these a huge threat to small businesses.
Spambots
Bots are applications designed to perform repetitive tasks. When used maliciously, they are often designed to spread spam messages or posts which could potentially get your business’s email or social media accounts banned.
Trojans
Also known as Trojan Horses, these malware applications are disguised as legitimate software that you might want to download. But once you install them on your device, they carry out the intentions of the cybercriminal that programmed them. This could range from destroying to distributing your sensitive information.
Backdoors
This type of malware is closely related to a Trojan Horse or worm. Once installed, it automatically executes its function – to create openings known as backdoors for cybercriminals to slip into your system through. Some are even undetectable to the user.
Keyloggers
Once this type of malware is installed, it tracks and reports every single thing you type back to the hacker that created it. This is usually designed to collect usernames, passwords, credit card information, PINs, and other data that might then be used for fraud or further cybercrime.
Keyloggers are sometimes used for legitimate purposes by corporations in order to monitor usage of people on their network and devices.
Ransomware
This type of malware takes over your network and places it behind a wall of encryption. The cybercriminals then demand a ransom payment in exchange for the encryption key. They usually threaten to destroy the data if you don’t pay up.
If you have current and relevant backups, you can simply wipe your system, ensure it’s clear of all malware, and then restore those backups. If your business doesn’t back up its data reliably or regularly and you fall victim to a ransomware attack, you could be in trouble.
These are especially popular right now, so we suggest you prioritize secure backups if you haven’t already.
Browser Hijackers
Browser Hijackers target your internet browser rather than your data storage. Once installed, they alter your browser settings. Usually they place adware in your browser on every page load, but sometimes they completely redirect your search activity to sites they want you to see and click on.
Rogue Antiviruses
A specific kind of Trojan Horse, rogue antivirus or security software purports itself to be legitimate security software. When it is installed, this malware actually targets and disables your other legitimate security software to make you more vulnerable to other avenues of cyberattack.
Viruses
Named after biological viruses because of their resemblance, computer viruses infect devices and networks and then reproduce and spread rapidly. Once they are installed, they begin their processes, often without the user knowing.
They can destroy or corrupt data and slow down or irreparably damage infected devices. And if the initial computer is connected to a network, the carnage can spread from one device to another quite easily.
Computer Virus 101
Once a device is infected with a computer virus, the virus will replicate and spread itself as far as it can within the computer or its network before it is detected and stopped.
These malware applications are a serious threat to the integrity and security of any organization they infect. Worse still, they come in many shapes and sizes and are constantly evolving.
In the following paragraphs we’ll detail some of the more common viruses and how they work.
Did you know you can get a virus on your smartphone by scanning the wrong QR code? Learn more here!
Macro
Macros are programs written in a specific language that applications like Microsoft Word or Excel understand. When you open a file containing a macro, they run automatically. These have been co-opted by bad actors, who send infected files containing malicious macros that run automatically when the document is opened. Be careful not to open files from senders you don’t recognize.
Boot Sector
A boot sector virus is a type of virus that targets the startup files of your computer. You get it the same way you get any other computer virus, but it doesn’t start causing problems until you boot up your computer the first time after you contract it. At that point, it wreaks its havoc on your device and network, potentially rendering it inoperable.
Polymorphic
This type of virus is a particularly nasty little bug. They replicate like any other virus, but they are constantly changing themselves and encrypting the different versions as they go. This makes it incredibly difficult to detect and stop each version of the virus, and gives it more time to damage your system.
Web Scripting
One of the most common forms of virus, a web scripting virus is usually spread via malicious pop-up or webpage ads. When clicked, the virus uses a client code script to breach your browser security and begin its process of infecting your device.
File Infecting
File infecting viruses, or file infectors, target the executable portions of your program files, and inject their code there. Then, each time you open any of those programs, you reinfect your device with the virus.
Resident
This type of virus lives in your computer’s memory. It infects and spreads through files you open that are stored on your hard disk, which makes them one of the more insidious viruses, and can be incredibly difficult to remove from an infected device.
Overwrite
These viruses get their name from what they do, which is overwrite original program data. This effectively replaces the original system code and bakes the virus into your system. If you remove it without replacing the original code, it renders the device inoperable.
Multipartite
A multipartite virus uses multiple parts of other viruses and their strategies to infect a computer. They combine the startup file targeting of a boot sector virus with the program targeting of other viruses to infect both parts of your system simultaneously.
Spacefiller
This type of virus is also sometimes called a cavity virus. It attempts to install itself only in the empty spaces of a file, which makes it undetectable if you’re looking at the size of all your normal files. This allows the virus to replicate and spread secretly.
Direct Action
Direct action computer viruses are sneakily embedded into legitimate programs or files. When you download and install or open the program or file they are hidden in, the direct action virus pops out and begins infecting your computer. You may be none the wiser because what you’ve downloaded will do exactly what you expect it to.
Have you heard about stealth viruses? Read up on them here!
Protect Your Small Business
So, you’ve learned that all viruses are malware but not all malware are viruses. And you’ve learned about the different types of each and how they infect your devices. But how do you prevent infection?
Number one: You need a comprehensive and up-to-date antivirus software to monitor for the things you can’t catch. And you need it on every company device!
Number two: It’s crucial that everyone in your business knows what to look out for and how to avoid opening or downloading anything suspicious. Ensure that you are having regular refreshers for everyone.
If you would like to enquire about our antivirus of choice, Fortinet’s Security Fabric, or how to get your staff invested in cybersecurity, please schedule a meeting with us! The experts here at CloudNexus will get you sorted out, no problem.